Original Article Link:
https://twitter.com/dilationeffect/status/1663136716662915073
Mainstream exchanges and institutions undoubtedly invest significant resources in network security. Dilation Effect cannot ascertain the internal security levels and implementation details of these institutions. Out of curiosity, we attempt to analyze the wallet addresses of these institutions based on publicly available information. By observing the subtle details, we consider whether these addresses pose potential security risks from the perspective of ordinary users and assess the extent of potential risk exposure.
The data for this flash analysis is sourced from public services such as Etherscan and Debank.
1. Selection of Analysis Targets
We examine the Top 1000 Accounts on Etherscan and select the tagged institutional addresses.
2. Selection of Analysis Dimensions
Given the lack of understanding regarding the technical details of wallet generation and management by these exchanges and institutions, how can we analyze the security of these addresses? In this analysis, Dilation Effect focuses on analyzing the contract approval status of these addresses.
It is common for addresses to be deceived by malicious contracts or to fall victim to vulnerabilities in approved contracts, resulting in stolen funds. Limiting approval amounts and regularly cleaning up approvals have become best security practices. So how do these large exchanges handle the approval of their addresses? Let’s randomly select a few addresses for analysis.
Case 1
Address: Binance 8 (0xF977814e90dA44bFA03b6295A0616a897441aceC)
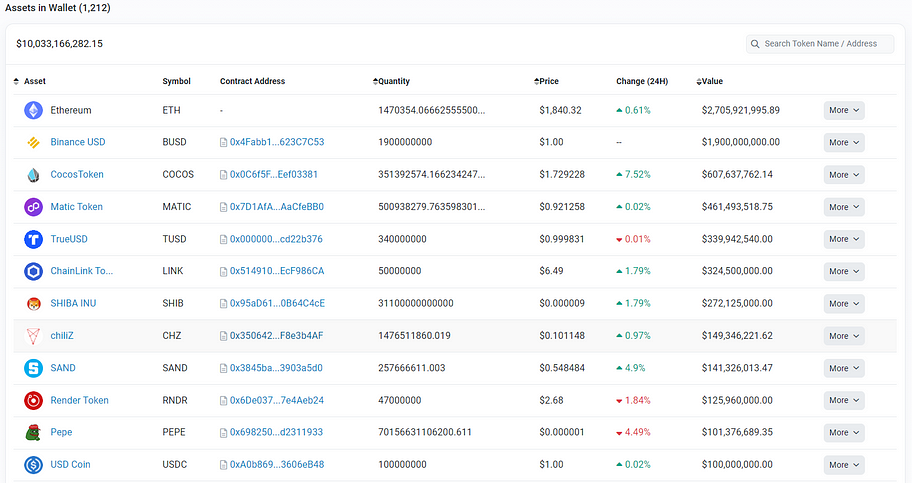
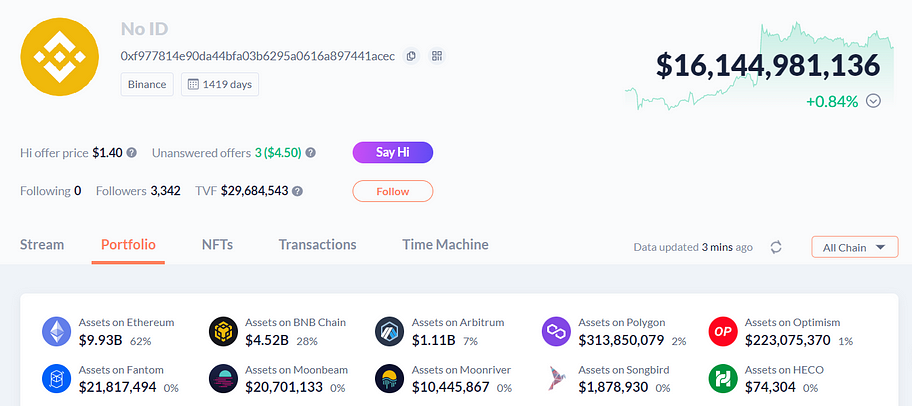
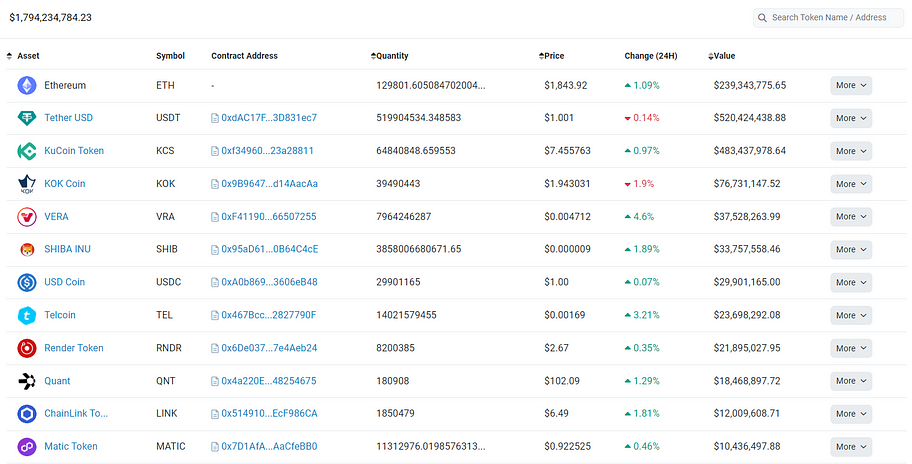
This is the largest wallet address in terms of balance on Binance, with a total balance of $10 billion on the Ethereum and $16.1 billion across other chains. The screenshot of some assets is as follows:
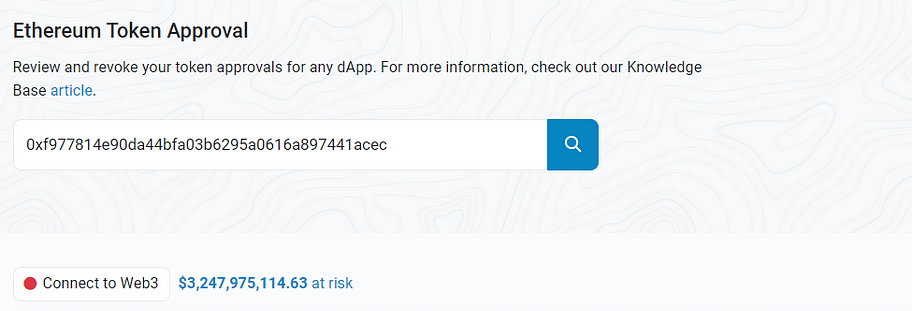
When examining the contract approval status of this address on the Ethereum, it indicates a potential risk of $3.2 billion. However, this does not necessarily imply a definite security risk; it is merely a description of the potential risk exposure.
Let’s take a closer look at how this address handles approvals, such as which tokens are approved to which contracts and the approval amounts. The following are selected excerpts from the query results:
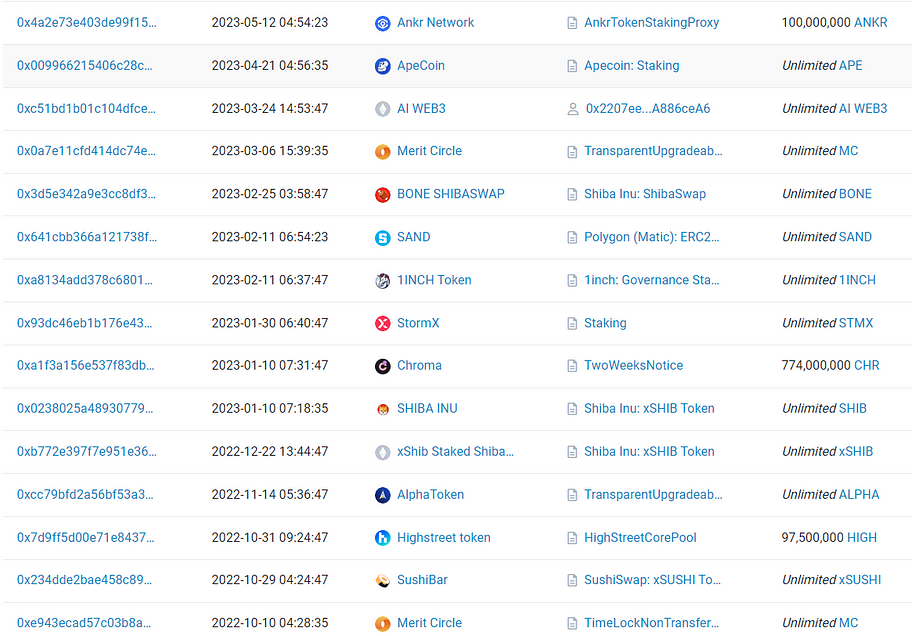
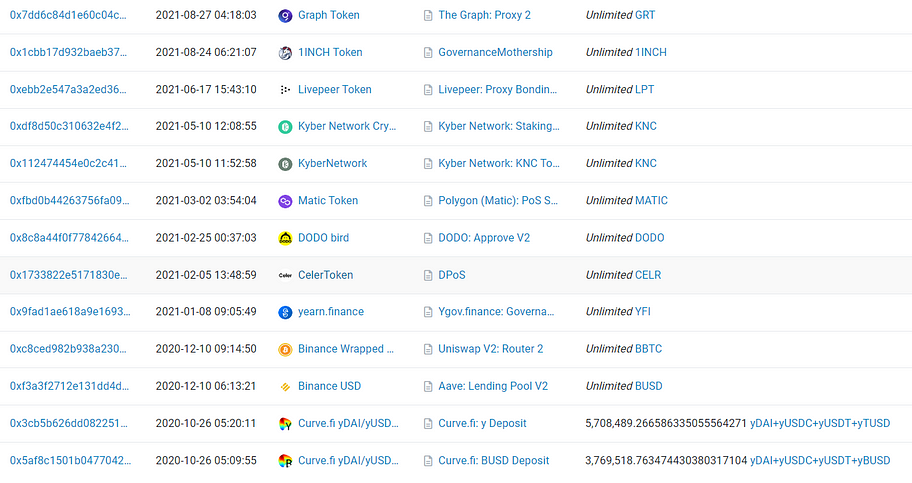
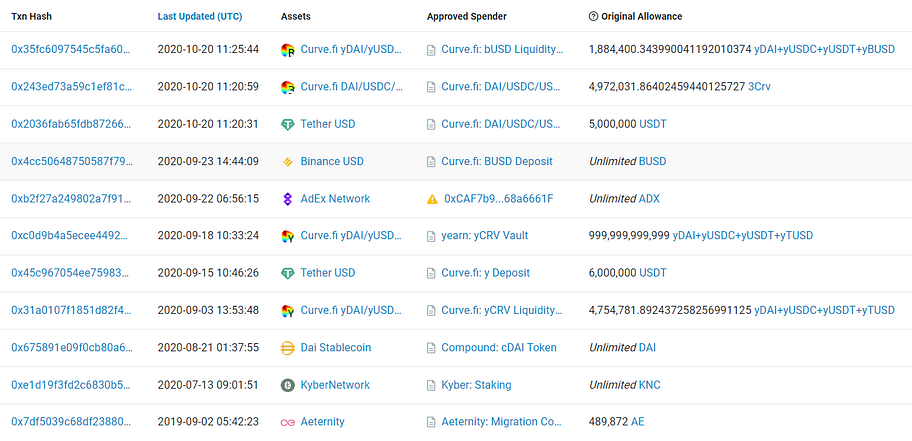
At this point, we notice a peculiar phenomenon: some tokens on this address have limited approval amounts, while others have unlimited approval amounts. The approval amount rules do not appear to be consistent. We pay special attention to the tokens with significant balances: BUSD, Matic, SHIB, and SAND. The balances for these tokens are $1.9 billion, $460 million, $260 million, and $140 million, respectively. The related approval records are as follows:
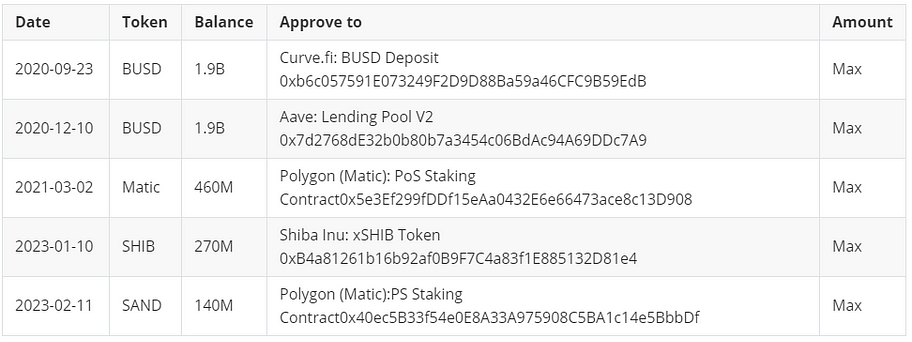
There are several obvious issues:
First, there is no regular cleaning of approvals for contracts. For example, regarding the approval for BUSD, more than two years have passed without any cleanup. This indicates that Binance lacks comprehensive system coverage in managing this aspect of internal security. Some may argue that an analysis of the relevant approved contracts revealed limited operations that can be performed, thus relatively safe. However, we want to emphasize that this is not simply a technical issue; it is more a matter of security management. Specifically, how Binance can comprehensively and systematically manage the risks associated with third-party contracts. We believe that a more rigorous and in-depth approach is possible. In fact, if you look closely, you’ll find that Aave: Lending Pool V2 is an upgradable proxy contract. Suppose (and this is purely hypothetical) the Aave contract were to be attacked. In that case, a loss of $1.9 billion would occur.
Second, a large number of cryptocurrencies have unlimited approval limits. In the event of an extreme scenario where the corresponding contract is attacked, having limits on the approval amount would reduce the risk accordingly. This also highlights the lack of systematic coverage in Binance’s internal security management in this aspect. Of course, one could argue that these are extreme cases, but in the history of the crypto industry, many low-probability events have occurred. We need to increase our sensitivity to risks and maintain a strong aversion to risk, which is essential.
Third, there is no uniformity in the approval rules for different cryptocurrencies. Some cryptocurrencies have limits on the approval amount, while others have no restrictions at all, indicating a lack of clear internal security management operations or coordination within the internal team at Binance.
Additionally, we are curious as to why addresses with such significant asset balances frequently engage in DeFi contract operations. Can Binance implement more granular address planning and isolation designs?
Reply from Binance: The team is optimizing the stake process to reduce any potential smart contract risks. The security team has set different authorization limits for different currencies, and will revoke the stake permission after each contract is completed. But Binance want to clarify that in different stake projects, different restrictions will be set for different coins, so the authorization rules for a certain coin/project will not be completely consistent.
Case 2
Address: Kucoin 6 (0xD6216fC19DB775Df9774a6E33526131dA7D19a2c)
This is the address of the Kucoin exchange, with $1.7 billion on the Ethereum network and a total of $1.9 billion on other chains. The asset balance screenshot of this address is shown below:
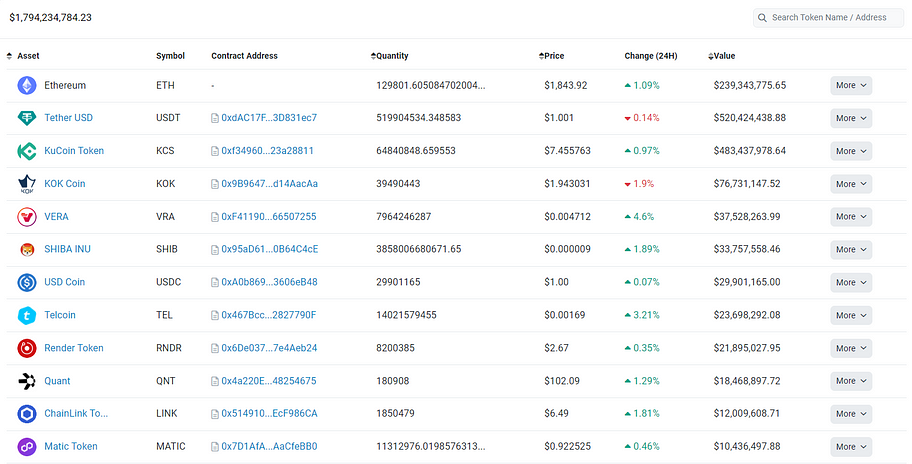
Checking the contract approval status of this address on the Ethereum network reveals a risk of $1.1 billion. Similarly, this does not necessarily indicate the presence of security risks but describes a possibility of potential risk exposure.
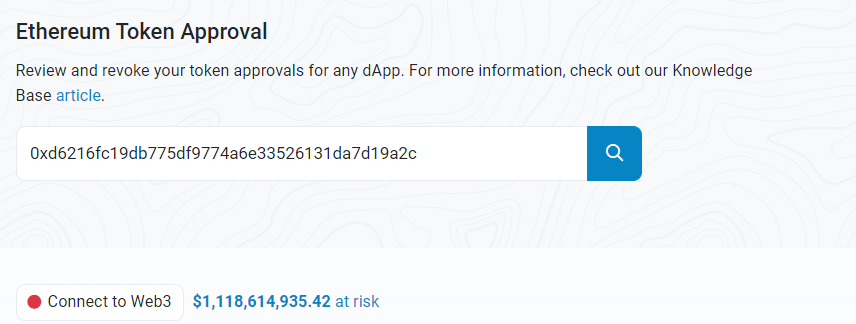
Now let’s take a closer look at the approval status of this address on Kucoin.
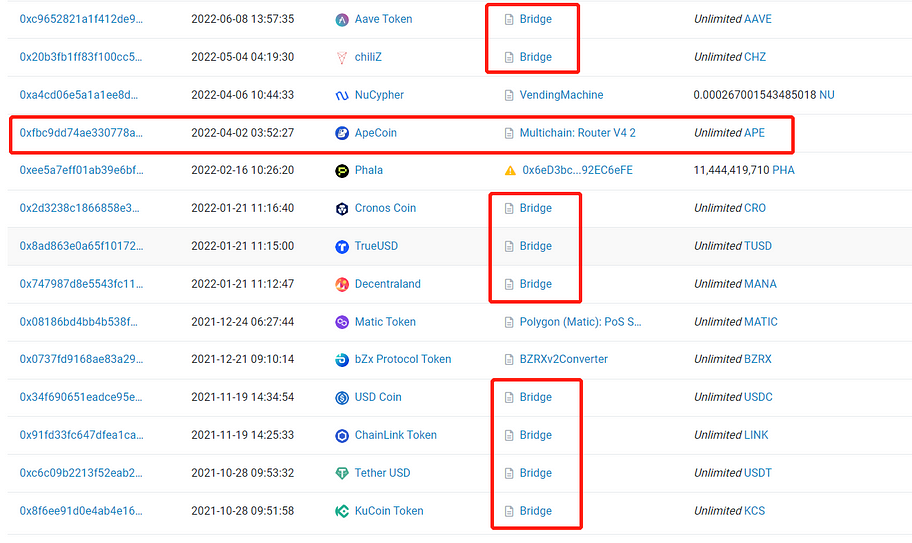
Wow! We have discovered some interesting things.
1. The APE token in this address was approved to the Multichain cross-chain Router contract on April 2, 2022. As we know, Multichain recently experienced an event beyond its control, but Kucoin did not immediately cancel the approval for the Multichain contract. This indicates that Kucoin still has room for improvement in risk emergency response.
2. Large amounts of USDT ($500 million), USDC ($290 million), KCS ($480 million), and other cryptocurrencies in this address were all approved without any limits to a contract called Bridge. After a simple analysis, we found that Bridge is a cross-chain bridge contract for Kucoin’s community chain KCC. However, upon checking the official website of KCC, we did not find any related security audit reports, which is concerning. Does anyone still remember the 2 million BNB attack on the BNB Chain?
Case 3
Address: Jump Trading (0xf584F8728B874a6a5c7A8d4d387C9aae9172D621)
This is the address of the institution Jump Trading, with $140 million on the Ethereum network and a total of $150 million on other chains. The asset balance screenshot of this address is shown below:
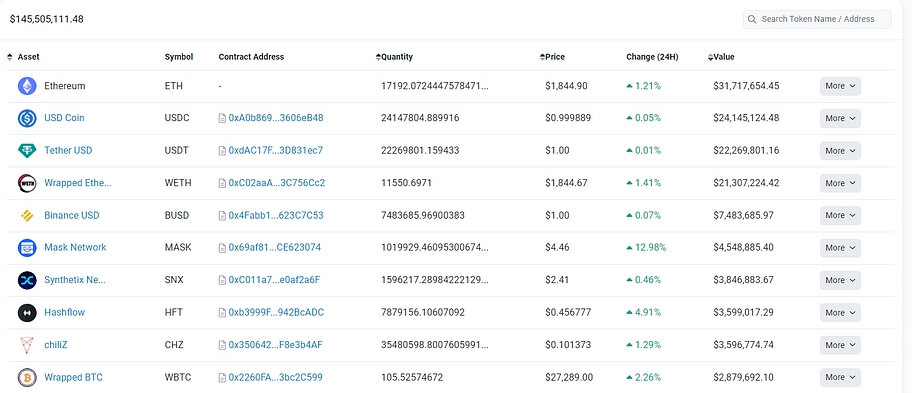
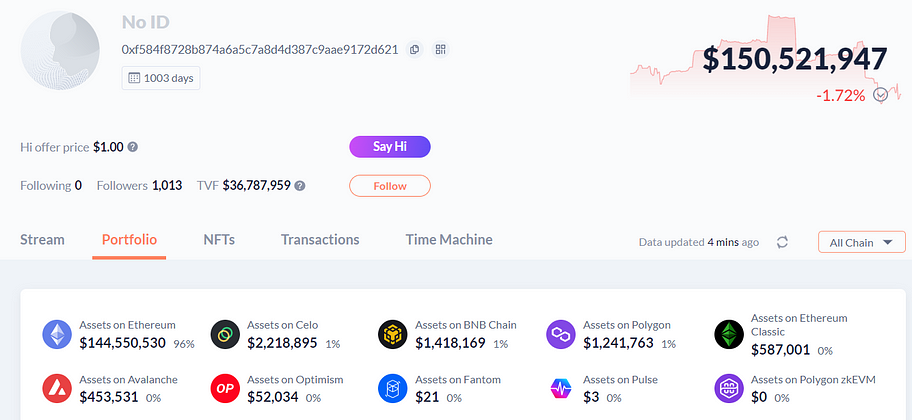
Checking the contract approval status of this address on the Ethereum network reveals a risk of $25 million. Similarly, this does not necessarily indicate the presence of security risks but describes a possibility of potential risk exposure.
Now let’s take a closer look at the approval status of this address on Jump Trading.
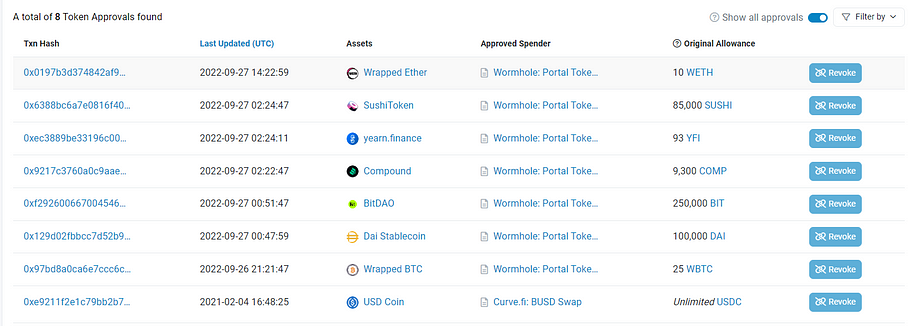
It can be observed that there are not many approvals for the cryptocurrencies in this address, and most of the approvals have set limits, indicating overall good management.
However, the USDC was approved to the Curve contract on February 4, 2021, without setting a limit, and it has not been canceled since then. This should serve as a reminder that if there is no need for corresponding contract operations, it is recommended to cancel the approval for this contract immediately.
Summary
This flash analysis concludes here. Dilation Effect randomly selected several exchange and institution addresses for analysis, and the results show that these institutions have not performed perfectly in terms of contract approval. We hope our analysis can provide reference for the relevant institutions. Exchanges and institutions whose addresses were not selected can also refer to the analysis process mentioned above to check for similar issues.
About Dilation Effect
Dilation Effect is a recently established Web3 security community composed of cybersecurity enthusiasts from around the world. It focuses on sharing objective and neutral Web3 security viewpoints.
Dilation Effect was the first in the industry to raise awareness about the risk of asset theft when using shared Apple IDs to download wallet applications on iPhones. It also exclusively disclosed the potential risks of Prime Protocol, a DeFi cross-chain lending protocol invested by Jump, and the Prime Protocol team has made rapid fixes.
Dilation Effect will continue to publish various Web3 security viewpoints, assess the security of Web3 products and protocols, provide timely and effective security reminders to ordinary users, and gradually provide free cybersecurity assistance to Web3 users.
Follow us on https://twitter.com/dilationeffect
Follow us
Twitter: https://twitter.com/WuBlockchain
Telegram: https://t.me/wublockchainenglish

